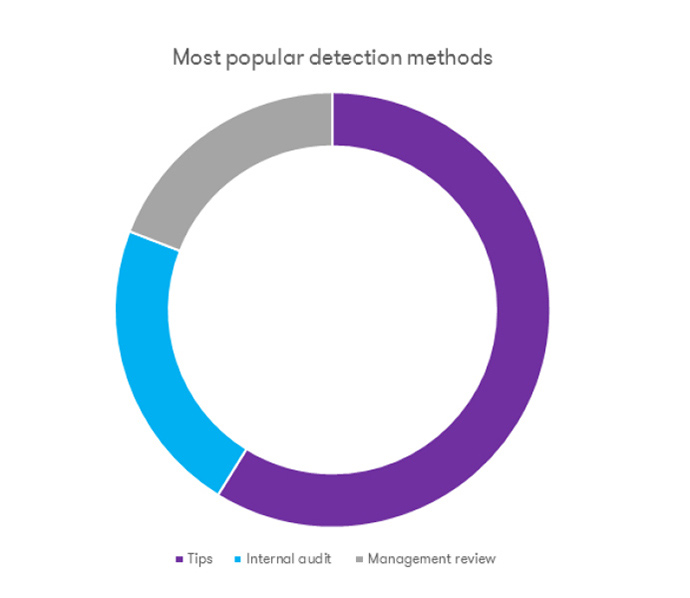
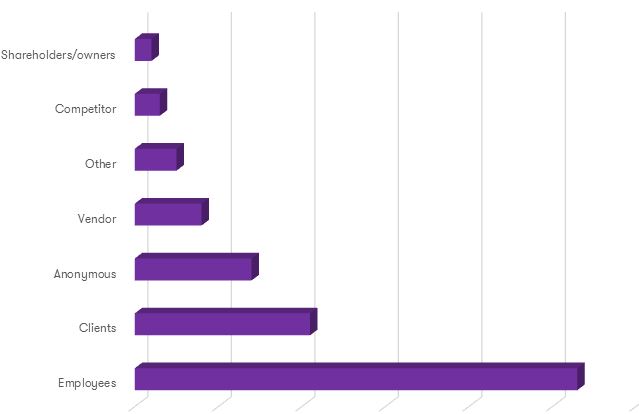
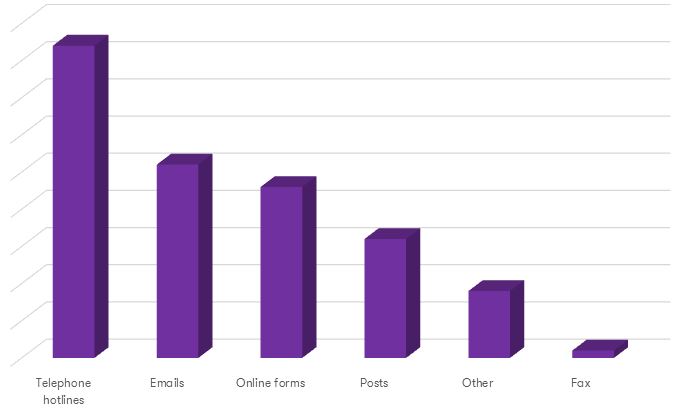
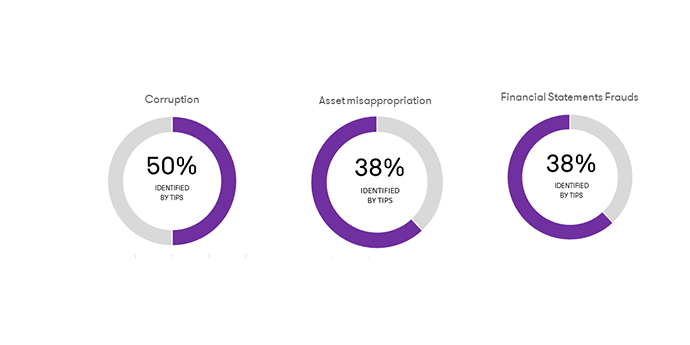
Services
Through Grant Thornton Financial Advisory Services we support the ambitions of dynamic businesses and help them grow
-
Transactional advisory services
Find out more about the transactional advisory services of Grant Thornton Financial Advisory Services
-
Valuations
Find out more about the valuations services of Grant Thornton Financial Advisory Services
-
Mergers and acquisitions
Find out more about the merger and acquisition services of Grant Thornton Financial Advisory Services
-
Forensic and investigation services
Find out more about the forensic and investigation services of Grant Thornton Financial Advisory Services
-
Recovery & reorganisation
Find out more about the Recovery & reorganisation services of Grant Thornton Financial Advisory Services
-
Business risk services
Find out more about the business risk services of Grant Thornton Financial Advisory Services
-
Business consulting
Find out more about the business consulting services of Grant Thornton Financial Advisory Services
-
Capital market
Capital market
We assist businesses in developing tax-planning strategies to optimise the tax burden in compliance with the regulation in force
-
Corporate and business tax
Find out more about our corporate and business tax services.
-
Direct international tax
Find out more about our direct international tax services.
-
Global mobility services
Find out more about our global mobility services.
-
Indirect international tax
Find out more about our indirect international tax services.
-
Transfer pricing
Find out more about our transfer pricing services.
-
Litigation
Our lawyers and accountants can manage all defense measures provided not only by the Italian law, but also by EU regulations and conventions
-
Family business
Find out more about our Family business services.
-
Legal
The client can be assisted in every need and with the same care both on important operations or disputes and on simple matters
Related insights:


Press release
Deliberate market focus drives solid growth
Deliberate market focus drives solid growth for Grant Thornton
Through Grant Thornton Operations we help businesses focus on their core business and improve efficiency
-
Back office outsourcing
Find out more about our Back office outsourcing services
-
Business process outsourcing
Find out more about our business process outsourcing services.
-
Compilation of financial statements
Find out more about our compilation of financial statements services.
-
Tax compliance
Find out more about our tax compliance services.
-
Electronic invoicing
Find out more about our electronic invoicing services
-
Electronic storage
Electronic storage is an archiving procedure that guarantees the legal validity of a digitally stored electronic document
-
Revaluation of corporate assets
Find out your civil and fiscal revaluation of tangible, intangible and financial assets
We provide tailored consulting on labor, HR, welfare, and industrial relations.
-
Payroll
Complete and customized payroll service, integrated with digital solutions and compliant with Italian and international regulations.
-
Labor consultancy
We help Italian and international companies manage all aspects of their workforce.
-
HR & Payroll Advisory Services
We review contracts, payroll, and risks for extraordinary transactions and we assess tax, labor, and safety risks in outsourcing contracts.
-
Extended services
We provide integrated digital tools to simplify HR management.
-
HR Infinity Portal
The HR Infinity Portal is Zucchetti’s platform designed to centralize communication between the company and its employees.
we can provide our clients with dedicated services aimed to increase the maturity and resilience of their businesses
-
Cybersecurity
GT Digital helps clients structure information security management internal functions, also through partially or totally outsourced functions
-
Agile and Programme Management
GT Digital provides support in the adoption and implementation of different portfolio management
-
Robotic Process Automation
Our “BOT Farm” can rely on digital workers able to help clients in routine activities, allowing employees to deal with more added-value activities
-
Data strategy and management
GT Digital can support clients in seizing the opportunities offered by Big Data, from the definition of strategies to the implementation of systems
-
Enterprise Resource Planning
We support clients in selecting the most appropriate ERP System according to their specific needs, helping them also understand licensing models
-
IT strategy
GT Digital supports clients in making strategic choices, identifying innovation opportunities, comparing themselves with competitors
-
IT service management
We can support with software selection and with the implementation of dedicated tools for the management of ICT processes
-
DORA and NIS 2
The entry into force of the DORA Regulation and NIS2 represents a major step towards the creation of a harmonised regulatory framework