How to detect an occupational fraud
23 Jul 2018Occupational frauds: how they are detected
How occupational fraud is detected
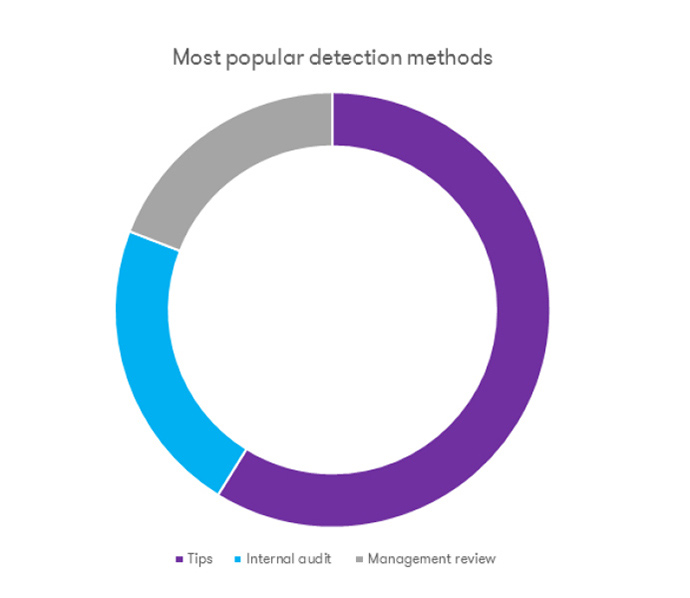
The survey ‘Report to the Nations 2018’ published by ACFE highlights that, since 2010 – the first year of publication of the series of reports by ACFE – in most cases (68%) frauds are detected by i) tips, ii) internal audit and iii) management review. Tips are the most popular detection method (40% of cases).
Mainly, tips were provided by employees of victim organizations (53%), followed by those coming from people outside the organization, such as suppliers and competitors (32%).
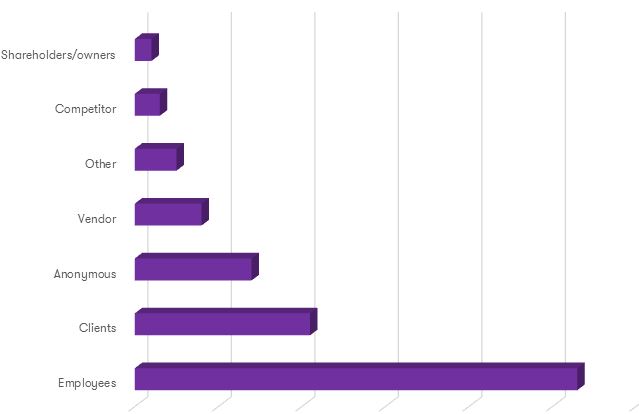
Moreover, 14% of tips came from an anonymous source, usually for fear of backlash.
During the years, the creation of dedicated hotlines has contributed to increase the number of tips. The survey also highlights that organizations with hotlines have suffered smaller fraud losses than those without this kind of reporting tools.
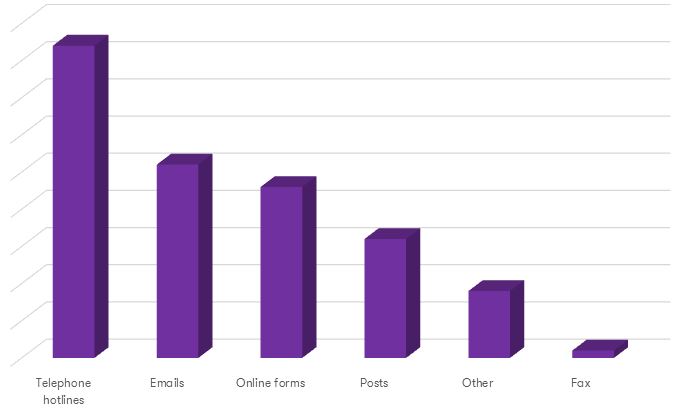
Although dedicated hotlines are most popular (42%), tips are also provided through other channels: emails (26%), online forms (23%), mailed letters (16%), fax (1%) and other (9%). Additionally, when a specifically codified reporting method is not used, employees usually report to: direct supervisors (32%), executives (13%), fraud identification teams (13%), colleagues (2%) and internal audit teams (10%).
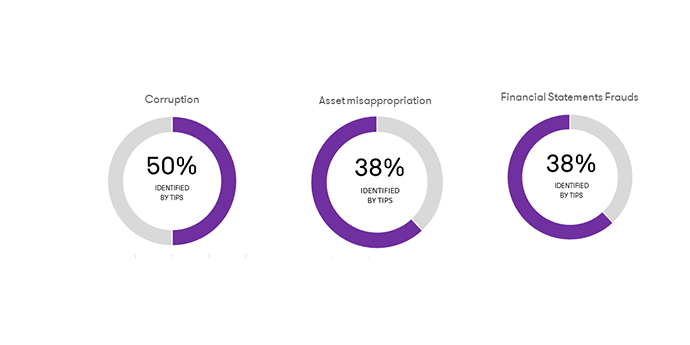
Corruption is particularly likely to be detected by tip (50%), followed by asset misappropriation and financial statements frauds (both at 38%).
Detection methods are strictly connected to the median losses suffered and the duration of the fraud scheme. Indeed, the more an organization works proactively to identify potential red flag situations, the smaller the losses suffered and the shorter the period between the fraud inception and its detection.
The ACFE survey grouped detection methods into three categories: active, passive, potentially active or passive. Active detection methods include a deliberate search of potential illicit or unlawful conducts within the organization or an internal control specifically designed to detect frauds.
Passive detection methods include cases in which the organization discovers the fraud by accident, confession or notification by law enforcement. The cases in which frauds are detected by external audit or tips are classified as potentially active or passive detection methods because those mechanisms might or might not involve a proactive effort to identify fraud, depending on the circumstances.
The takeaway message of this analysis is that organizations have to implement tools, instruments and procedures to identify quickly potential risky conducts that might turn into frauds, thus reducing the impact in term of losses.
To this extent, an organization can prevent or at least limit the impact of frauds by implementing the following actions:
Dissemination of clear corporate rules as a deterrent
Fighting the risk of frauds requires a twofold approach: communicating to all the people in the organization that specific controls are in place to detect potential fraudulent conducts and clarifying to all the people in the organization which conducts are accepted or prohibited as well as the sanctions the company will apply in case of illicit conducts.
Identification of weaknesses and loopholes in the system
Weaknesses can be detected when the internal controls designed to prevent the improper or non-authorised use of corporate assets do not work properly.
Understanding key internal controls efficiently is possible when corporate processes are well-known and there is a deep awareness of the different types of frauds and perpetrators. Consequently, the management has to identify the key internal controls capable of preventing frauds in every business areas and understand the level of efficacy of those controls.
Understanding the company business and the relevant procedures
It is key for the management to have a deep and full understanding of the company business and the relevant procedures, foreign entities and subsidiaries, supply procedures and non-core business activities. A scarce understanding of the business, of the procedures and of the existing controls might expose the company to the risk that a fraud occurs.
In most companies, data and information are generally processed and transmitted electronically. It is vital that a company knows where these data and information are stored, how they are treated or processed and the risks that might arise from their losses or dissemination to third unauthorised parties. Moreover, an organization shall ascertain that the existing procedures and controls are actually implemented to protect the use and treatment of those data and information.