In today's environment, characterized by increasing digital interconnectedness and increasingly globally distributed supply chains, third-party cyber risk management has become an indispensable element of organisations' security strategies. The fact that 48% of data breaches in 2024 were estimated to be caused by vulnerabilities arising from access or relationships with external providers confirms how these players represent a privileged entry point for cyber criminals. Faced with this scenario, it is no longer sufficient to rely on sporadic compliance audits or static partner assessments: it is necessary to adopt evolved technological solutions and structured processes capable of ensuring dynamic, continuous and proactive management of the entire third-party ecosystem.
Most cyber-mature organisations have already integrated advanced tools into their strategies to gain real-time visibility into the risk level of their suppliers and partners. However, these platforms alone are not sufficient to handle the growing complexity of an ever-expanding attack surface involving cloud environments, IoT/OT devices, legacy systems, and third-party applications. For this reason, Grant Thornton proposes a holistic and integrated approach, combining the latest monitoring and detection technologies with governance, advisory and operational response services.
Central to this proposition is Cybersonar, a proprietary platform that combines Threat Intelligence and Attack Surface Management capabilities, enabling continuous monitoring of the external attack surface and early identification of vulnerabilities, misconfigurations and emerging threats, not only for the organisation but also for its critical third parties. Cybersonar enables organisations to anticipate attacks, strengthen the resilience of the entire digital ecosystem and ensure compliance with regulations such as NIS2 and DORA, which are increasingly relevant across multiple industries. This platform integrates seamlessly with other leading technology solutions such as Cyberhunter, the proprietary SIEM & SOAR system that enables the automation of detection and response processes, and Defprobe, an NDR solution designed for anomaly and threat detection across enterprise networks, cloud and IoT/OT environments. To complete the ecosystem, Grant Thornton offers innovative tools for predictive brand protection, removal of fake sites and content, confidential dark and deep web searches, as well as AI chatbots that can be customised for specific security needs.
However, technology alone is not enough: to ensure comprehensive protection, Grant Thornton complements its proprietary platforms with a comprehensive portfolio of professional services. In the area of Cybersecurity Governance, companies can count on Cybersecurity Advisory services, the definition of security strategies and governance models (Cybersecurity Strategies & Governance), CISO as-a-Service support, the management of compliance processes with standards and laws such as ISO 27001, NIS2, DORA and GDPR, as well as the development of Security Policies and customised procedures. Particular attention is paid to the Security by Design phase, so that security is integrated from the earliest stages of product, application, and service development. On the technical side, Grant Thornton provides Cyber Defence services such as vulnerability assessment, penetration testing on networks and web applications, secure code review, forensic activities on digital, mobile and IoT/OT environments, threat modelling, targeted cyber threat intelligence and security posture assessment in complex cloud environments. In the event of an incident, companies are supported by specialised Incident Response & Forensics teams that can intervene quickly to contain, analyse and resolve even sophisticated and large-scale events.
All these capabilities converge in a state-of-the-art Security Operations Centre (SOC), equipped with Managed Detection and Response (MDR) and Network Detection and Response (NDR) functions, for continuous surveillance of IT/OT environments, automated alert management and timely incident response. To support data and access protection, Identity and Access Management (IAM, IGA, PAM), Data Loss Prevention (DLP), Network Access Control (NAC) and Email Security Gateway solutions are also available, which are essential to reduce the internal attack surface and prevent the loss or exfiltration of sensitive information. Lastly, to mitigate one of the most significant risks, i.e., the human factor, Grant Thornton offers structured Cyber Security Awareness programmes tailored to raise awareness and train staff on secure behaviour, phishing simulation, credential management and incident response.
The experience gained with numerous customers confirms that the real challenge is not only technical, but also governance-related: IT security must move beyond the strictly IT sphere to become a leadership, risk management and governance, corporate culture and awareness objective. In Italy, as highlighted by the CLUSIT 2025 Report, awareness is growing, but the gap compared to the maturity levels of other European countries is still significant. Italian companies are starting to shift their focus from technological tools towards governance, investing in organizational models, training and risk assessment. This change is necessary to keep up with the constantly evolving European regulatory context. The NIS2 Directive represents one of the most important security and compliance issues for all organizations operating in strategic sectors within the European Union. However, the most recent available data show that full compliance with NIS2 is still a distant goal for many Italian companies: in fact, only 61% of those that have launched a structured initiative are in line with the requirements.[1]
Too commonly, companies show fragmented models, unclear roles and an underestimation of the impact of the supply chain: NIS2 makes these aspects a priority today. In this phase, many organizations are starting assessment and gap analysis activities, often together with ISO/IEC 27001:2022 certifications to structure effective and measurable processes. Thanks to its multidisciplinary experience and widespread presence across the territory, Grant Thornton has already successfully supported some Italian companies in starting their NIS2 implementation process. In particular, our teams have conducted in-depth assessments on various organizational levels, from governance to the supply chain, precisely identifying gaps with respect to regulatory requirements and proposing concrete, sustainable and calibrated action plans on the specific context of each company. These interventions subsequently became operational roadmaps that allowed customers to arrive prepared and anticipate regulatory deadlines, increase their IT resilience and strengthen the trust of internal and external stakeholders.
Further recognition of our commitment and expertise in the sector is represented by the ISO/IEC 27001:2022 certification, which attests to the excellence of our information security management system. This result not only consolidates our leadership in the field of cybersecurity but also represents a concrete guarantee for our collaborators: working with a certified partner means relying on professionals who operate according to the highest international standards. Furthermore, the ISO/IEC 27001:2022 certification allows us to transfer proven methods, structured governance and already tested tools to our clients, thus accelerating the compliance process (not only towards NIS2, but also towards other recent regulations such as DORA in the financial sector).
Our goal is not just compliance, but the construction of a solid cybersecurity system, capable of generating value and protecting the business in the long term. In a rapidly evolving regulatory landscape, Grant Thornton represents a reliable partner supporting Italian companies in the transition from a reactive approach to a strategic and proactive cybersecurity vision. Adapting to NIS2 is not just an obligation: it is a responsible choice, which strengthens operational resilience and stakeholder trust.
From a market point of view, the cybersecurity sector is experiencing an unprecedented expansion. The global market was estimated at $245.62 billion in 2024 and is expected to reach $500.70 billion by 2030, with a compound annual growth rate (CAGR) of 12.9%[2]. The trend is very positive in Italy, too: in 2024, the national market reached 2.48 billion euros, recording a 15% increase % compared to 2023. Among the most dynamic sectors are logistics, transport and services, which, favored by the implementation of the NIS2 Directive, recorded above-average increases by 25% and 24%, respectively[3].
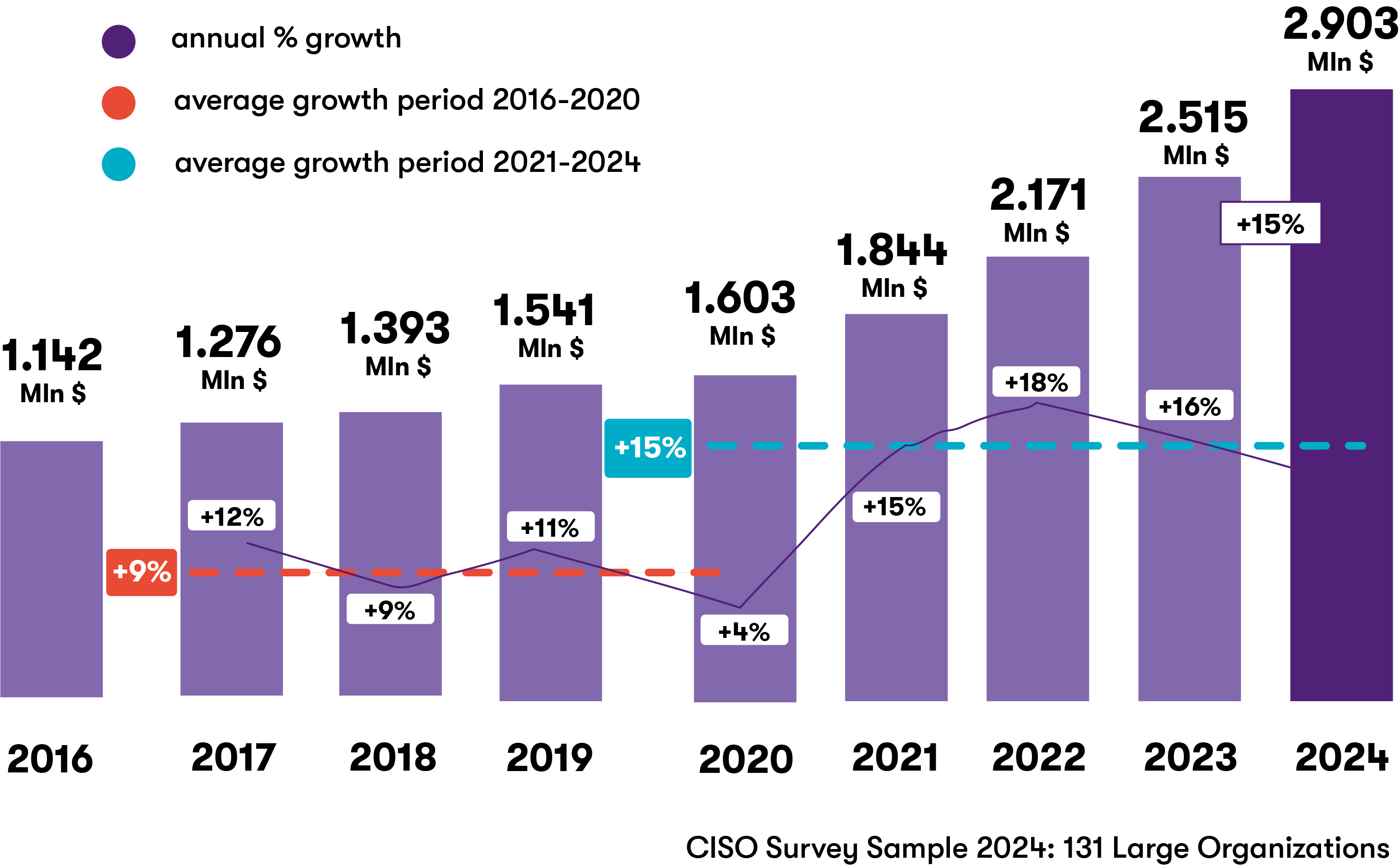
These figures demonstrate a structural transformation in the perception and management of digital risk, fueled not only by new regulations, but also by a greater awareness of the strategic importance of cybersecurity. Companies that know how to promptly invest in structured, integrated and governance-oriented solutions will gain competitive advantage, and be able to count on greater operational resilience, better market positioning and higher credibility towards customers, investors and partners.
[1] ANGI – Associazione Nazionale Giovani Innovatori. Cybersecurity Observatory: only 61% of companies that have started a structured project towards NIS2 are compliant, 2024.
[2] Grand View Research, Cyber Security Market Report, 2024.
[3] Cybersecurity & Data Protection Observatory – Politecnico di Milano, The cybersecurity market in Italy: it grew by 15% in 2024, 2024.